The name PayPal has become synonymous with the most popular method of Internet payment. Everyone knows of PayPal and many, many people use it. And why not? Having a secure and private method of payment online has been an incredible resource. For many of us, eBay was the first online store where we first heard about PayPal, and over the years, eBay and PayPal have had a comfortable relationship. Well, in late 2015 eBay and PayPal will be severing their ties as PayPal moves on from eBay and out on their own.
This leaves PayPal open to join with someone else. Enter Apple Pay. Apple Pay is Apple’s new payment option through its app featured on Apple products like the new iPhone 6 or iPhone 6 Plus. PayPal is not only popular, but also easy to use for its customers. Here’s how it will work: iPhone users will find the PayPal app, locate the store on the app, and sign themselves in. This is done while the user is in the store, ready to make their purchase. It will be that easy. In order for the payment to go through, the iPhone user will be required to aim their phone directly at the point of payment within the store, put their finger on the Touch ID option, and then the transaction will be complete. Basically, point and shoot. A confirmation of a successful transaction will be in the form of a beep and a vibration.
So now let’s talk about the security of paying through PayPal and the Apple Pay app. The security that has been implemented for iPhone users to utilize this paying option is of the highest caliber. The benefit of having this payment option is mainly so that you don’t have to show your personal credit card information while in the store and run the risk of having your personal credit and identity breeched somehow. That said, both Apple and PayPal had to make sure that your personal credit card and bank information was extremely secure. According to PayPal, the personal information and credit card numbers of its users are “heavily guarded, both physically and electronically.” We trust their word, and they ensure to do whatever it takes to continue to guard this information.
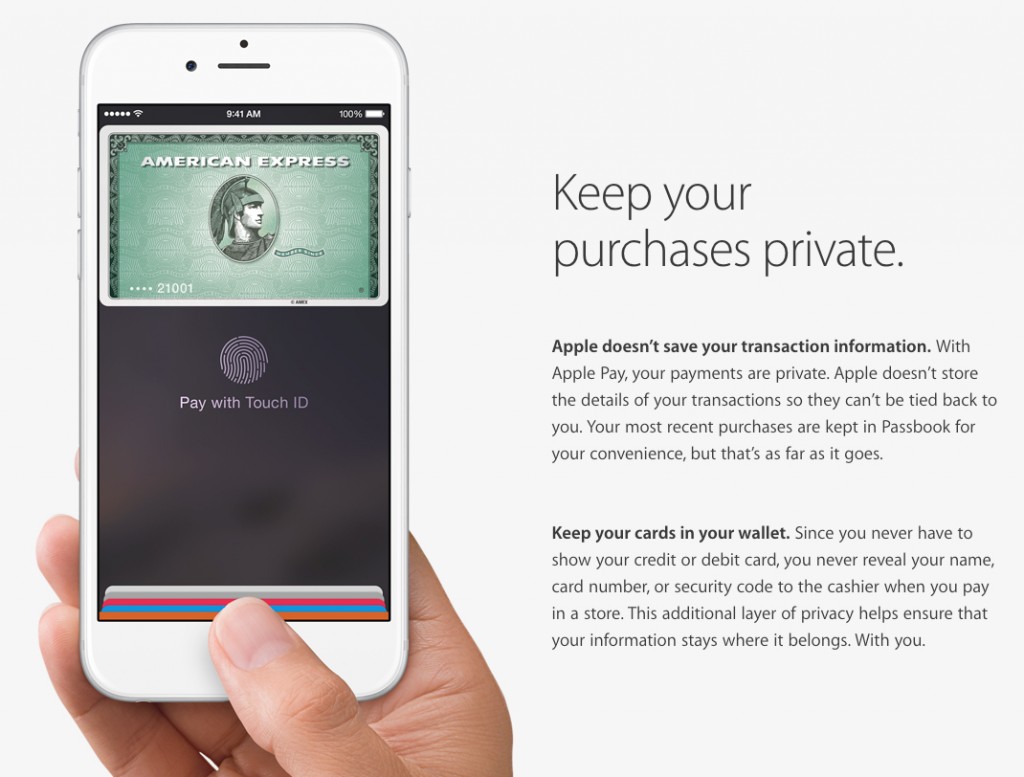
In addition, PayPal’s servers are not directly connected to the Internet, in an effort to prevent hackers from getting to that information. The only eyes that see your personal information and transactions is you, especially when you receive an email immediately after each purchase or payment through PayPal. This way, you have the ability to keep track of what is going on with your account.
Likewise with Apple Pay, your personal credit card numbers and information is secure and not seen by Apple or the employees in the stores. The way Apple Pay functions is “users take a photo of their credit card and add it to their phone’s Passbook where it is assigned a unique device account number, encrypted and stored in the phone’s Secure Element Chip.” The individual security code and the number of the device you are using will be the two items needed to complete the purchase. According to the company, “Apple will never know what you purchased, and you’ll still get rewards points on the credit cards you use.”
With all of that purchasing power in one place, there is also a protection for you if you lose your iPhone. This protection is the Find my iPhone feature. A misplaced or lost iPhone’s information can be erased completely if it’s not in the owner’s hands, and this way your private information will not be accessed by criminals.


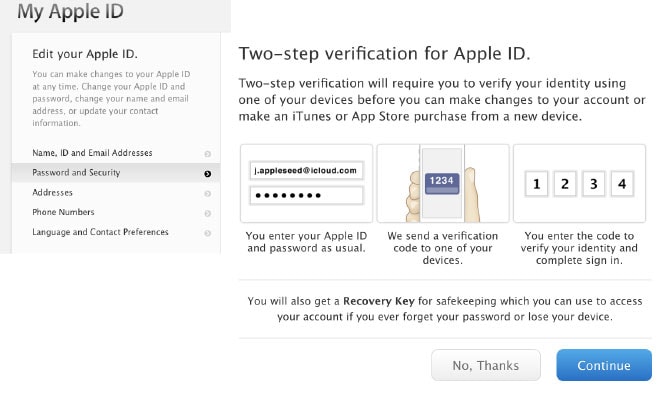
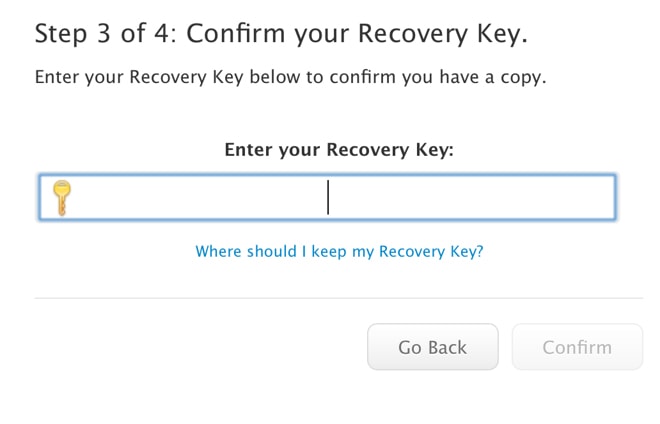 Now a general warning: If you manage to forget your password, throw away your recovery master key AND lose access to all of your “trusted” devices, you will not be able to login to the Apple ID system, period. No exceptions. Apple Corporation will officially not be able to help you, but a customer service representative can recommend replacement devices for you to buy.
Now a general warning: If you manage to forget your password, throw away your recovery master key AND lose access to all of your “trusted” devices, you will not be able to login to the Apple ID system, period. No exceptions. Apple Corporation will officially not be able to help you, but a customer service representative can recommend replacement devices for you to buy.
